Factoring MFA into your security plans
Multi-factor authentication (“MFA”) provides an additional layer of security to ensure that only you can access your account—even if someone knows your password. The way MFA works is that it requires two pieces (or “factors”) of evidence—usually something you know (e.g., a pin or password) and something you have (e.g., a device or security key)—to prove you’re the person who should be granted access to an account. If you know the pin and have the device, Presto!, you’ll be able to enter.
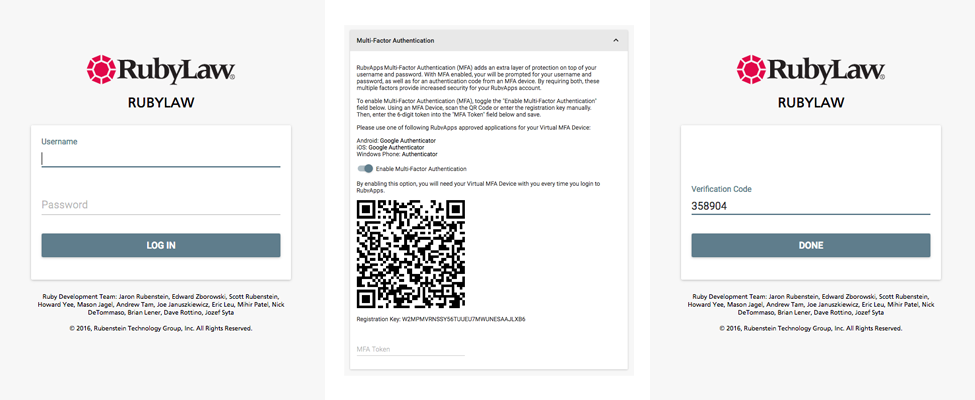
With RubyApps, and most online accounts with MFA, it works the same way: you enter your username and password on the login screen; the service will ask you to authenticate by providing the a temporary, time-sensitive code (the “second factor”), and (if authenticated) you’ll be able to access the account.
Why is MFA important?
These days, a password alone isn’t enough. With security breaches becoming regular news, having an additional layer—for your personal and professional accounts—is critical. Take your primary email account as an example. If some bad actor takes it over, he can reset the password, read and delete your emails, respond using your email and impersonate you, and potentially access other confidential information and put you and your reputation at risk. If they take over your email, they can then reset your password on external systems (like RubyApps) and gain access to your firm content. But with MFA in place, they would also need to have access to your second factor, your mobile phone, to actually login to RubyApps.
You may already be obeying best practices for email; but, consider the risk to institutions such as law and professional services firms where privileged information must be kept secure and confidential.
Different types of MFA
MFA isn’t one specific thing, so we’ll cover a few different types below.
SMS and phone verification
SMS and phone verification works by texting (or calling) you and listing a sequence of numbers (a “code”). These then get typed into the website you’re trying to access. Remember, these codes typically expire within a few minutes, so don’t dilly-dally!
TOTP MFA
While SMS and phone verification is convenient, since most people have functional “second factor” devices, it’s not the most secure. A safer method of MFA is Time-based One-Time Password (TOTP) MFA. Using Google Authenticator (and similar apps) to generate time-based codes, this type works like SMS and phone verification only (a) it will ask for your TOTP code after you’ve entered your username and password and (b) it’s more secure. The numeric code changes every 30 seconds or so. This is the form of MFA that RubyApps supports.
U2F security keys
Universal Second Factor (U2F) security keys look like the name describes: they’re small devices fit onto actual keychains and may be used as second factors. What’s neat about the U2F approach is that, unlike the previous two methods, this one can only be validated by a single device—your specific key. In this sense, U2Fs meet the dual criteria of “something you know” and “something you have.”
The way these work is that when a service asks for your second factor, you will plug your authentication device into your computer (or the device through which you’re trying to access a website) and the key will validate the authenticity of the website URL, generate a validation code, and then send it back to site you’re trying to access. This method is the top way to “plug and play.” It’s not only the most secure, but it’s the fastest. RubyApps can support U2F security keys via your corporate Single Sign-On (SSO) solution, if desired.
How can I learn more?
If you’ve been reading our Spotlight on RubyLaw series, you can learn more about about Multi-factor Authentication (MFA) in our recent edition on tools for remote teams. If you’re a RubyLaw client, you can also reach out to our Support team or your RubyLaw representative to schedule a conversation.









